Natas9
Website URL: http://overthewire.org/wargames/natas/natas9.html
According to the data on the OverTheWire webpage.
Username: natas9
URL: http://natas9.natas.labs.overthewire.org
Let’s log into the URL for Natas8
Let’s see the source code.
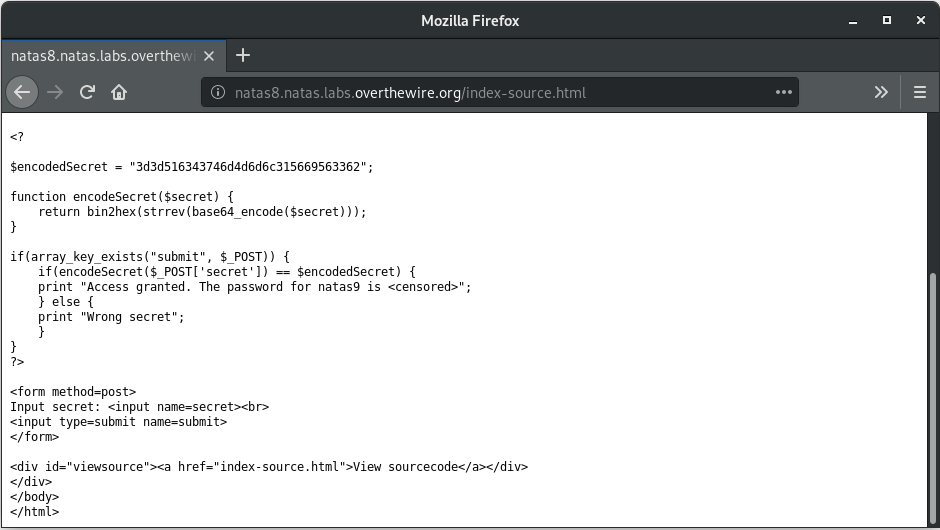
So the algorithm seems to be performing operations on the string we provide. The sequence of operations is as follows:
base64encode -> reverse the string -> bin2hex
At the end of the operations, the string that should result in “3d3d516343746d4d6d6c315669563362“. So the simple task for us is to apply the sequence in reverse. That’ll get us the string we need to send to obtain the password.
I’ll prefer to write up a quick small program to do the task.
import base64
def main():
cipher = '3d3d516343746d4d6d6c315669563362'
plaintext = base64.b64decode((cipher.decode('hex')[::-1]))
print plaintext
return
if __name__ == '__main__':
main()On running the code, we get the secret as: “oubWYf2kBq”. Let’s send that over to the server.
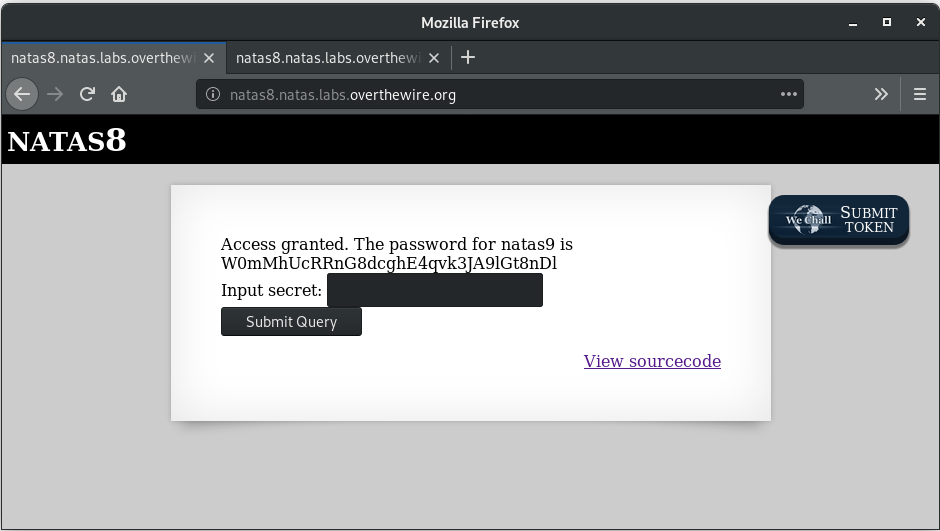
Done!
Password for next level: W0mMhUcRRnG8dcghE4qvk3JA9lGt8nDl