Bandit33
Website URL: http://overthewire.org/wargames/bandit/bandit33.html
The task is as follows:
After all this
gitstuff its time for another escape. Good luck!
Finally! A task that is not git. Let’s log into the server as bandit32
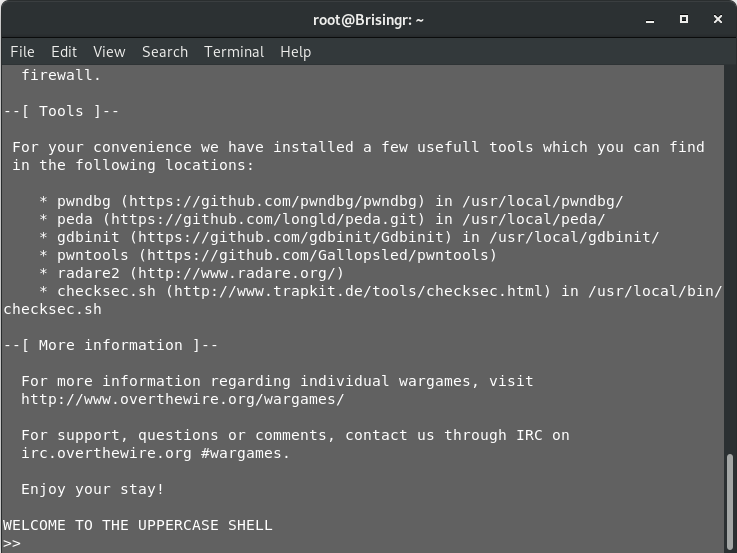
Well, it seems that this drops us into some kind of shell. Let’s try and find out more about it. First of all, I’ll try a few commands, to get a hang of what the shell’s accepting.
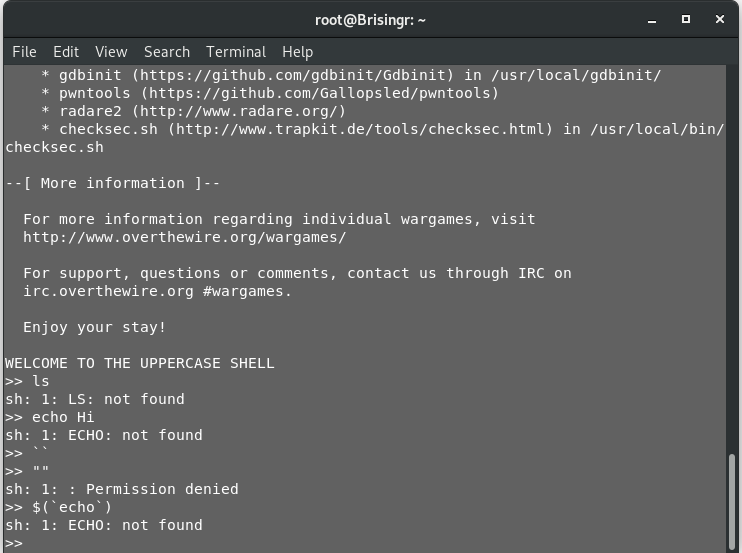
This shell program seems to be converting any input string to uppercase and trying to execute it. So, we need to either find a command that is comprised of all uppercase characters, or something that cannot be converted to uppercase (Note that the quotation marks and the dollar sign are not throwing up errors).
Now, the last attempt we made, $(echo)throws up an error on the “echo” and not the dollar sign. Dollar sign in shell scripting is very useful. We can try using that. Let’s find out the number of arguments that have been used to trigger the script
$#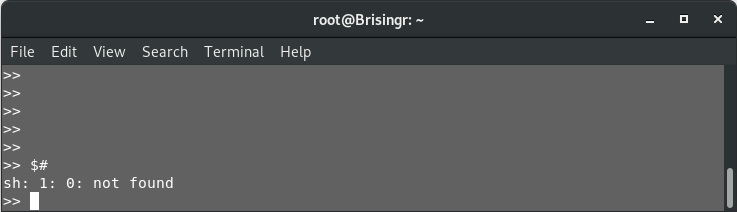
So, it seems there are no arguments being passed while triggering this shell program. However, $0 will be the program name. Let’s try that.
$0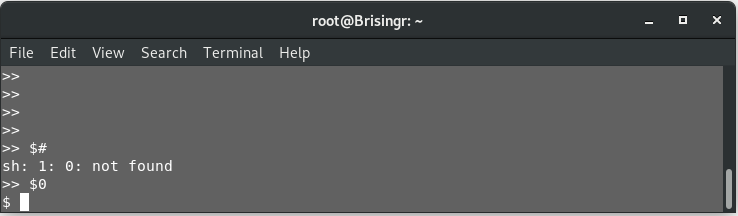
Woah! We got a shell prompt! Let’s see under what permissions.
whoami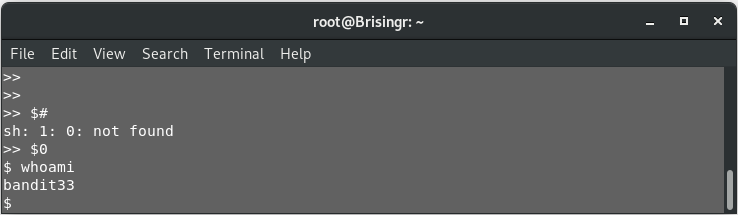
Well then, the rest should be easy enough.
cat /etc/bandit_pass/bandit33Mission accomplished!