Bandit27
Website URL: http://overthewire.org/wargames/bandit/bandit27.html
Let’s log into the server as bandit26
We do have to keep in mind the lessons learnt in the previous task. Logging into the bandit26 shell will throw us into a restricted shell, so, the only way we can actually accomplish anything is by using the same method, i.e. triggering more and then getting the shell from inside it. You can revise it if you want here
The task is as follows:
Good job getting a shell! Now hurry and grab the password for bandit27!
Let’s see the current directory contents.
ls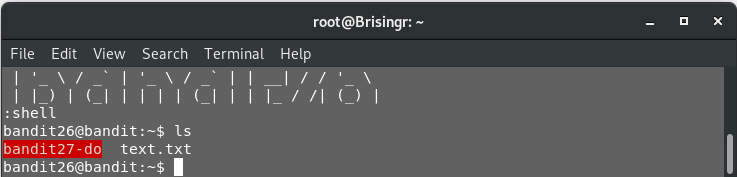
The text.txt, is the same one that is opened as a part of our default shell fro bandit26, and therefore of little use to us. The other file, bandit27-do seems familiar. If you recall, in one of our previous tasks (here, to be precise).
It let’s us execute a command with the permissions of another user. Hence, we will do that to get the password for bandit27 from the /etc/bandit_pass directory.
./bandit27-do cat /etc/bandit_pass/bandit27Voila!