Natas11
Website URL: http://overthewire.org/wargames/natas/natas11.html
According to the data on the OverTheWire webpage.
Username: natas11
URL: http://natas11.natas.overthewire.org
Let’s log into the URL for Natas10
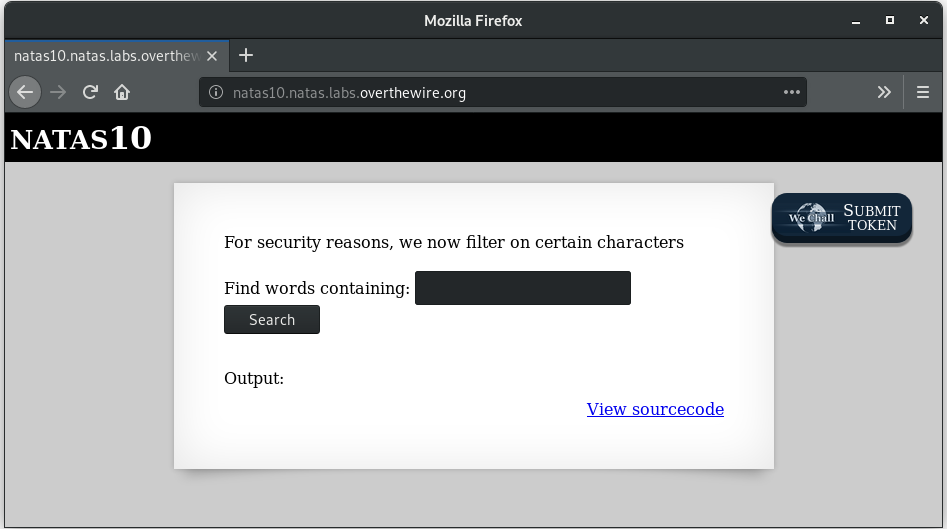
Ah! This one seems to have some input sanitization! Let’s have a look at the source code.
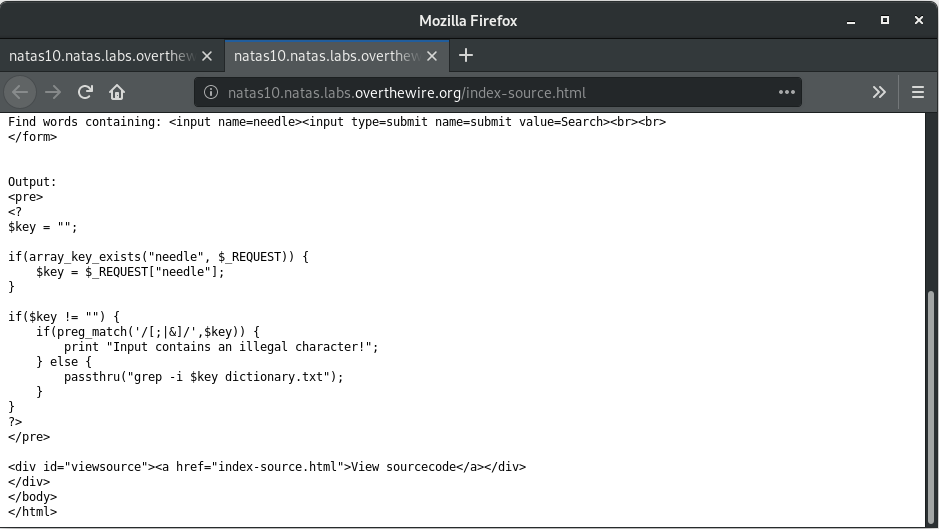
Okay, so the following characters are filtered out: ';', '|', '&'. Hmm, it seems all the common characters needed to escape the grep command seemed to have been filtered out.
Let’s have a look at the script again. Whatever input we give, it gets passed on to the grep command, assuming it doesn’t have any of the forbidden characters. How can we bypass it? Note that the forbidden characters list doesn’t include a space or a forward slash ‘/’. We can use this fact to redirect the grep command. So, if an input is 2 strings separated by a space, then the second string would be considered as a file path for grep to search in. Using this, we should be able to break the code. So, try giving an input “.* /etc/natas_webpass/*” to direct the grep to search in the appropriate directory as well.
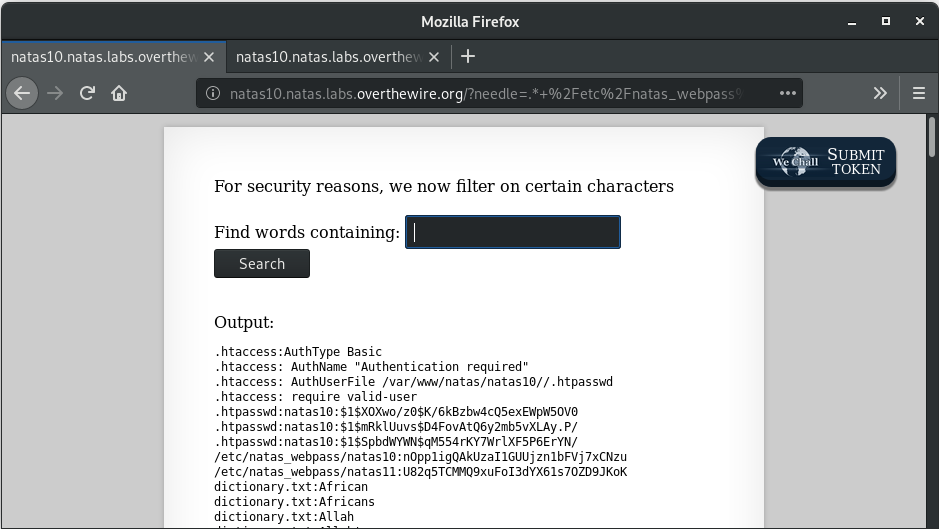
Sanitize it properly!
Password for next level: U82q5TCMMQ9xuFoI3dYX61s7OZD9JKoK