Bandit17
Website URL: http://overthewire.org/wargames/bandit/bandit17.html
Login using the credentials of bandit16, obtained in the previous level.
Let’s have a look at the task.
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.
This level seems to be more interesting than the previous ones. As the problem statement mentions, the first step we need to do is to scan for open ports and identify which of those support SSL.
We can use nmap with version detection for achieving this. The T4 flag is used to accelerate the scan speed somewhat.
nmap -sV -T4 localhost -p31000-32000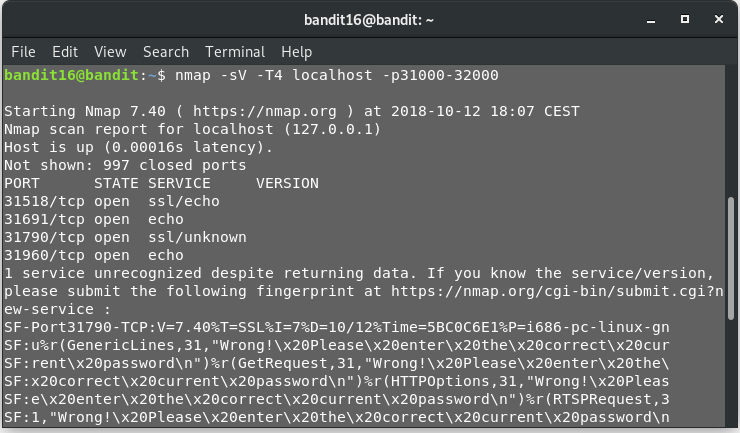
So we see that we have a total of 4 ports open:
- 31518
- 31691
- 31790
- 31960
Out of these, only 31518 and 31790 seem to support SSL. Furthermore, we observe that according to Nmap, port 31518 is having a echo service running. So, this means, port 31790 should be the one we want. Let’s try connecting to the port using s_client.
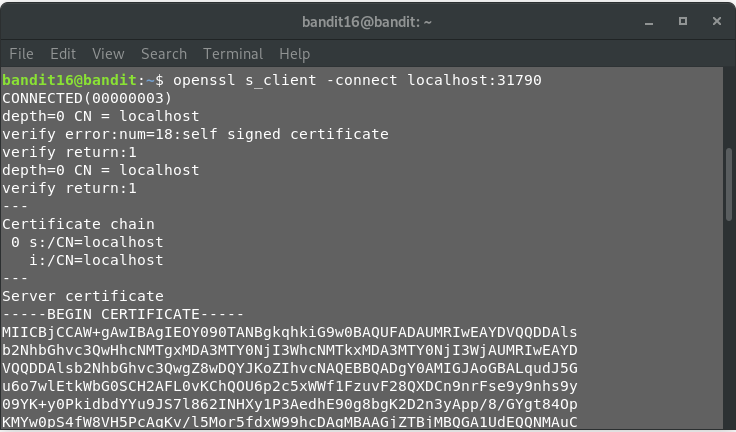
Let’s submit the password for current level
Done! We get an SSH key to access the next level.